Overview of Kubernetes RBAC
Kubernetes Role-Based Access Control (RBAC) is a security mechanism that provides a way to control access to Kubernetes resources based on the roles and permissions assigned to individual users or groups. RBAC allows you to manage access to Kubernetes resources such as pods, deployments, services, and namespaces, at a granular level.
In Kubernetes, RBAC is based on the following three key concepts:
- Roles: Roles define a set of permissions for a specific resource or set of resources in a namespace. For example, you can define a role that grants read access to pods in a namespace.
- RoleBindings: RoleBindings link a role to a user or a group of users. For example, you can create a role binding that grants read access to pods in a namespace to a specific group of users.
- ServiceAccounts: ServiceAccounts are used by pods to authenticate with the Kubernetes API and can also be assigned roles and permissions. For example, you can create a service account that has permission to create and delete pods in a namespace.
Using these RBAC components, you can define fine-grained access controls for users and groups based on their roles and responsibilities. RBAC enables you to limit access to sensitive resources, control privileges, and enforce the principle of least privilege. RBAC also allows you to delegate responsibilities to different teams or individuals without granting them full admin privileges, which can help improve the efficiency of your Kubernetes environment.
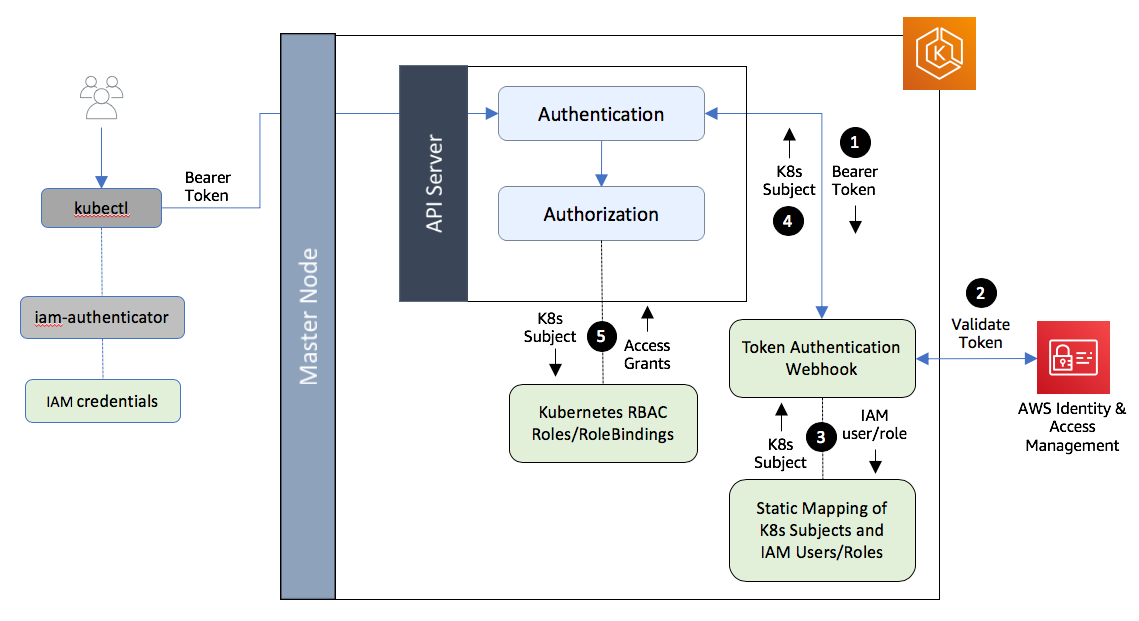
EKS-specific implementation of RBAC
In Amazon Elastic Kubernetes Service (EKS), you can implement Role-Based Access Control (RBAC) to control access to Kubernetes resources in a granular way. The RBAC implementation in EKS is similar to the standard Kubernetes RBAC implementation, with a few EKS-specific components.
To implement RBAC in EKS, you’ll need to define the following components:
- Roles: In EKS, you can define roles using Kubernetes Role objects. A Role defines a set of permissions for a specific resource or set of resources in a namespace.
- RoleBindings: In EKS, you can create RoleBindings using Kubernetes RoleBinding objects. A RoleBinding links a role to a user or a group of users.
- ServiceAccounts: In EKS, you can create ServiceAccounts using Kubernetes ServiceAccount objects. ServiceAccounts are used by pods to authenticate with the Kubernetes API and can also be assigned roles and permissions.
In addition to these standard Kubernetes components, EKS also provides the following components for RBAC:
- AWS Identity and Access Management (IAM) Roles for Service Accounts (IRSA): IRSA is an EKS-specific feature that allows you to associate an IAM role with a Kubernetes ServiceAccount. This enables you to grant IAM permissions to pods running in your EKS cluster, which can be useful for accessing AWS resources such as Amazon S3 buckets or DynamoDB tables.
- EKS Managed Node Groups IAM Roles: EKS Managed Node Groups (MNG) is a feature that allows you to launch and manage worker nodes in your EKS cluster. MNG also provides an IAM role for the worker nodes, which you can use to control access to AWS resources.
Using these RBAC components, you can implement fine-grained access controls in your EKS cluster to help secure your Kubernetes resources and AWS resources. It’s important to carefully plan and implement RBAC in your EKS cluster to ensure that each user or group has the appropriate level of access and to minimize the risk of security incidents.
Best practices for configuring RBAC in EKS
Here are some best practices for configuring RBAC in Amazon Elastic Kubernetes Service (EKS) and a code example:
- Use Role-based Access Control: Use Role-based Access Control (RBAC) to restrict access to Kubernetes resources based on a user’s role in your organization. Use roles and role bindings to grant or deny access to specific resources.
Example code for a Role:
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
namespace: my-namespace
name: pod-reader
rules:
- apiGroups: [""]
resources: ["pods"]
verbs: ["get", "watch", "list"]
Example code for a RoleBinding:
kind: RoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
namespace: my-namespace
name: pod-reader-binding
subjects:
- kind: Group
name: pod-readers
apiGroup: rbac.authorization.k8s.io
roleRef:
kind: Role
name: pod-reader
apiGroup: rbac.authorization.k8s.io
2. Use Least Privilege: Grant users only the permissions they need to perform their job functions. Avoid granting broad permissions that could allow users to access or modify resources they shouldn’t.
Example code for a Role that grants read-only access to a specific namespace:
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
namespace: my-namespace
name: read-only
rules:
- apiGroups: [""]
resources: ["pods", "services", "deployments"]
verbs: ["get", "list", "watch"]
3. Use Service Accounts: Use Kubernetes Service Accounts to provide an identity for pods running in your cluster. Use role bindings to assign roles and permissions to service accounts.
Example code for a Service Account:
apiVersion: v1
kind: ServiceAccount
metadata:
name: my-service-account
namespace: my-namespace
Example code for a RoleBinding that links a role to a service account:
kind: RoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: my-role-binding
namespace: my-namespace
subjects:
- kind: ServiceAccount
name: my-service-account
namespace: my-namespace
roleRef:
kind: Role
name: my-role
apiGroup: rbac.authorization.k8s.io
4. Use IAM Roles for Service Accounts (IRSA): Use IAM Roles for Service Accounts (IRSA) to grant pods running in your EKS cluster access to AWS resources.
Example code for an IRSA:
apiVersion: eks.amazonaws.com/v1beta1
kind: IAMRoleMapping
metadata:
name: my-iam-role-mapping
namespace: my-namespace
spec:
roleArn: arn:aws:iam::123456789012:role/my-iam-role
serviceAccountName: my-service-account
serviceAccountNamespace: my-namespace
By following these best practices, you can implement a secure RBAC configuration in your EKS cluster.
Common problems with RBAC in EKS
Here are some common problems that you may encounter when configuring RBAC in Amazon Elastic Kubernetes Service (EKS), along with code examples to help troubleshoot these issues:
- Incorrectly Defined Roles or RoleBindings:
One of the most common issues with RBAC in EKS is incorrectly defined Roles or RoleBindings. This can cause permission errors when trying to access Kubernetes resources. Make sure that the Roles and RoleBindings are defined correctly and have the necessary permissions. Here is an example of a RoleBinding that is incorrectly defined:
kind: RoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: pod-reader-binding
subjects:
- kind: User
name: my-user
roleRef:
kind: Role
name: pod-reader
In this example, the RoleBinding is referencing a Role named “pod-reader”, but the Role is not defined in the YAML configuration. Make sure that all the Roles and RoleBindings are defined correctly and have the necessary permissions.
2. Incorrectly Defined ServiceAccounts:
Another common issue with RBAC in EKS is incorrectly defined ServiceAccounts. This can cause errors when trying to authenticate and authorize Kubernetes resources. Make sure that the ServiceAccounts are defined correctly and have the necessary permissions. Here is an example of a ServiceAccount that is incorrectly defined:
apiVersion: v1
kind: ServiceAccount
metadata:
name: my-service-account
namespace: my-namespace
secrets:
- name: my-service-account-token
In this example, the ServiceAccount is missing the “imagePullSecrets” field, which is required to authenticate with private container registries. Make sure that all the ServiceAccounts are defined correctly and have the necessary permissions.
3. Incorrect Namespace:
Another common issue with RBAC in EKS is using the wrong namespace when defining Roles or RoleBindings. This can cause permission errors when trying to access Kubernetes resources in a different namespace. Make sure that the namespace is defined correctly and matches the namespace of the Kubernetes resource you are trying to access. Here is an example of a RoleBinding that is using the wrong namespace:
kind: RoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: pod-reader-binding
subjects:
- kind: ServiceAccount
name: my-service-account
namespace: wrong-namespace
roleRef:
kind: Role
name: pod-reader
In this example, the RoleBinding is referencing a ServiceAccount named “my-service-account”, but the ServiceAccount is defined in a different namespace than the RoleBinding. Make sure that the namespace is defined correctly and matches the namespace of the Kubernetes resource you are trying to access.
By understanding these common problems and using the appropriate code examples to troubleshoot them, you can successfully configure RBAC in EKS and manage access to Kubernetes resources effectively.
How to diagnose and troubleshoot RBAC issues
RBAC (Role-Based Access Control) is a security model that controls access to resources based on the roles assigned to users. RBAC is widely used in organizations to provide secure and controlled access to resources such as files, folders, applications, and systems.
RBAC issues can occur due to various reasons, such as misconfigurations, incorrect policies, conflicts, and errors in permissions and roles assigned to users and resources. Here are some detailed steps to diagnose and troubleshoot RBAC issues:
- Review Access Controls: The first step is to review the access control policies and roles assigned to users and resources. Ensure that these policies and roles are accurate and up-to-date. Check if the access controls are being applied as intended. Use the logs or audit trails to identify any inconsistencies or errors.
- Check Permissions: Verify that users have the correct permissions and roles assigned to them. Ensure that they are granted the correct level of access to the resources they need. Check if any new permissions have been added, or if permissions have been removed or modified.
- Check Group Membership: Ensure that users are added to the correct groups and that the groups have the necessary permissions to access the resources. Check if any users have been removed or added to groups, or if any group permissions have been changed.
- Check Configuration: Review the RBAC configuration, and check if there are any misconfigurations or conflicts. Ensure that all RBAC components are working as expected. Check if any new components have been added or removed, or if any configurations have been changed.
- Check Resource Ownership: Ensure that the ownership of the resources is correctly assigned. Resources must be owned by the correct users or groups to ensure that RBAC policies and roles work correctly. Check if any resources have been transferred or modified, or if any ownerships have been changed.
- Check Policies and Roles: Review policies and roles, check if they are defined correctly and grant access as intended. Ensure that they are not conflicting with each other. Check if any new policies or roles have been added or removed, or if any policies or roles have been changed.
- Check Application Logs: Check the application logs to identify any errors or exceptions related to RBAC. This can provide insight into any issues that may be affecting the RBAC system. Look for any error messages or stack traces related to RBAC.
- Use Test Scenarios: Test RBAC scenarios in a controlled environment to identify and resolve any issues. This can help you identify any issues before they impact production environments. Create test users and groups, and test access to various resources.
- Seek Expert Help: If you are still unable to resolve the RBAC issue, seek the help of an expert in RBAC or the application you are troubleshooting. RBAC issues can be complex and challenging to troubleshoot, and expert help may be required to resolve them.
By following these steps, you should be able to diagnose and troubleshoot most RBAC issues. Remember to document your findings and the steps you took to resolve the issue. This can help you in the future if you encounter similar issues.
Tips for optimizing RBAC for better performance and security
Here are some tips for optimizing RBAC for better performance and security:
- Use Role Hierarchies: Role hierarchies can simplify RBAC management by allowing roles to inherit permissions and roles from other roles. This reduces the number of roles and permissions that need to be managed. It also improves performance by reducing the number of checks that need to be performed.
- Use Role-Based Access Filters: Use role-based access filters to limit access to only the resources that a user needs to perform their job. This reduces the number of resources that need to be managed and improves performance by reducing the number of checks that need to be performed.
- Use Group-Based Access: Use group-based access to assign roles to groups of users. This simplifies RBAC management by reducing the number of roles that need to be assigned to individual users. It also improves performance by reducing the number of checks that need to be performed.
- Regularly Review Roles and Permissions: Regularly review roles and permissions to ensure that they are still needed and that they are assigned correctly. This reduces the number of unnecessary roles and permissions, which improves performance and security.
- Implement Role Segregation: Implement role segregation to limit the access of roles and permissions to specific areas or functions of the system. This reduces the risk of unauthorized access and improves security.
- Use Least Privilege: Use the principle of least privilege to limit the access of roles and permissions to only the resources and functions that are needed to perform a specific job. This reduces the risk of unauthorized access and improves security.
- Use RBAC Auditing: Implement RBAC auditing to track changes to roles and permissions, as well as access to resources. This provides visibility into RBAC usage and helps detect any unauthorized access or changes to RBAC policies.
- Regularly Test RBAC: Regularly test RBAC to ensure that it is working correctly and efficiently. This can include testing RBAC scenarios in a controlled environment, as well as performing RBAC performance testing.
By implementing these tips, you can optimize RBAC for better performance and security. Remember to document your RBAC policies and procedures, and to regularly review and update them as needed. This ensures that RBAC remains effective and efficient over time.
Conclusion
In conclusion, RBAC (Role-Based Access Control) is a critical security model that controls access to resources in EKS (Elastic Kubernetes Service) and other environments. Troubleshooting RBAC issues in EKS requires a systematic approach that involves reviewing access controls, checking permissions and group membership, reviewing configurations and policies, checking resource ownership, reviewing application logs, and testing RBAC scenarios.
To optimize RBAC for better performance and security in EKS, it is recommended to use role hierarchies, role-based access filters, group-based access, regular role and permission reviews, role segregation, least privilege, RBAC auditing, and regular RBAC testing. By implementing these tips, RBAC can be optimized to provide efficient and secure access control to resources in EKS and other environments.
